WWDC21’s principal security and privacy announcements
Last year, during WWDC20, Apple announced so many privacy-oriented features that this year I was all ears.
During the keynote, I was keeping a count of how many times they mentioned “encryption”, “security”, or “privacy”. Well, I counted 19 times! That's once every five minutes.
As someone who works in data security and cryptography, I deeply enjoy watching how Apple pushes developers and users into a more secure and privacy-respectful world year after year.

WWDC21 vs WWDC20
This is my third year of summarizing the most important security and privacy updates after the WWDC Keynote.
If you are feeling nostalgic, free to check out my previous posts from WWDC20 and WWDC19.
If I were to recommend one single video to watch from those two previous years – it’s this one: “Secure your app: threat modelling and anti-patterns”. It explains how to model app-specific threats and how to mitigate them with security controls. Those who want to dive deeper, check out my latest risk management workshop on Github.
User-oriented updates
This year, Apple announced a lot of updates and new features focused on the end user experience. Let’s go through some of them.
Digitalizing identity
- Digital ID in Wallet: Upload your passport into your phone. Looks intriguing, but I can’t even imagine when this feature will be available in Europe. Also, now losing your iPhone means losing everything – money, keys and ID :)
- Account recovery: A secure way of recovering your Apple ID using the help of one of your “trusted contacts”.
- Digital legacy: A way to transfer your account to your “trusted contacts” if anything bad happens to you.
- Updates to Find My: A Bluetooth-based network that enables you to locate your devices even when they are turned off. If you are curious what could go wrong because all Apple devices are connected through a single Bluetooth network, well, many things. Check out the post “Send My: Arbitrary data transmission via Apple's Find My network” by Fabian Bräunlein.
Protecting user privacy
Every year, Apple gives users more tools to protect their privacy, such as being able to opt out from tracking and hiding/masking their data.
- Private relay: A VPN+TOR-like service that encrypts user traffic from Safari, and then sends it through different internet networks, which hides the user’s IP address, location and browsing activity. It will undoubtedly complicate tracking done by other companies, but I guess Apple still knows a lot about the device owner.
- Mail privacy protection: It hides your IP address and location, and prevents senders from seeing when you opened an email.
- Safari privacy and App privacy reports: These reports help users see what websites or apps that have been accessing their data, when and how, and what domains apps have contacted. I expect much noise on Twitter when people see how many analytics services popular apps use.
- Hide my email: This feature enables users to use a unique “burner” email when registering on a website/app, instead of using their own, real email address. Last year, it was announced as “Sign in with Apple”, and honestly – I’ve been using it a lot. Now, this new email hiding feature will be integrated right into both Safari and Mail.
- On-device processing: Siri has learned how to process audio requests on-device, minimizing server-side usage. Photos has learned how to recognize text in pictures (OCR), which is also done locally. Plus, there have been additional updates to HomeKit Secure Video. Apple pushes developers to rely more on device capabilities, rather than sending data over the network.
For more user-oriented updates, see this Hacker News article, and watch the WWDC session “Apple’s privacy pillars in focus”.
Application security 101 for app developers
Apple continues their ongoing efforts to educate developers on how to build more secure and privacy-oriented apps.
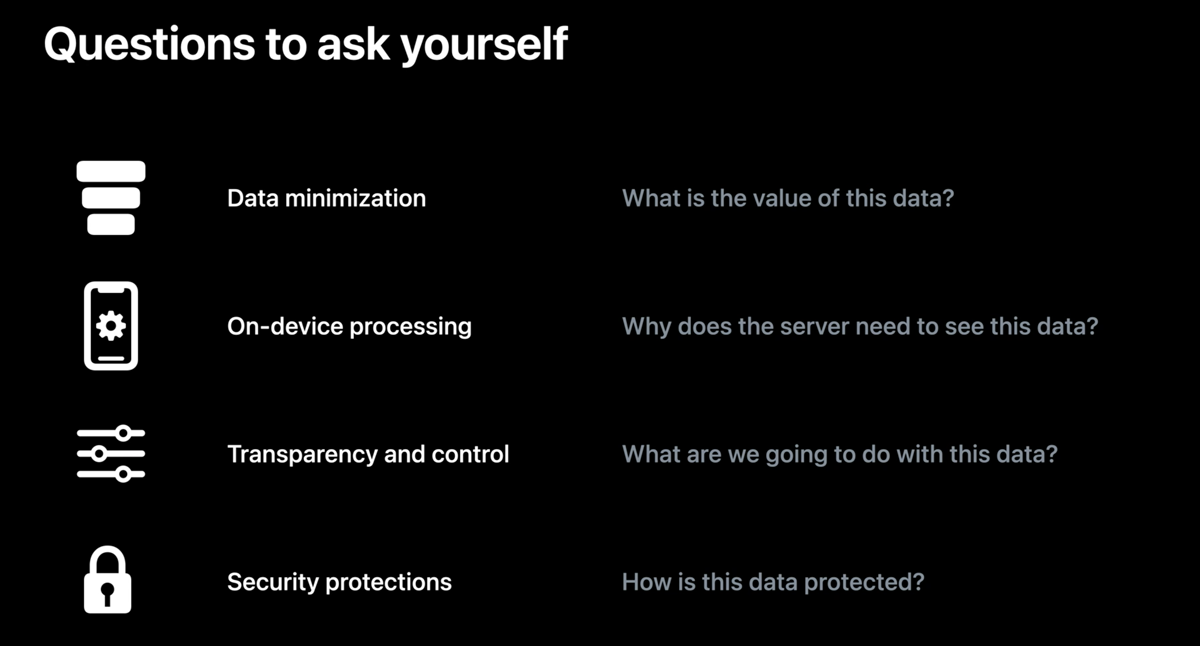
Both the keynote and the “privacy pillars” session that I mentioned above really emphasize these four steps:
- Data minimization (don't access more data than your app actually needs, and clean up the data after usage)
- On-device processing (process data locally within the app, and use end-to-end encryption when sharing data between devices/users)
- Transparency and control (give the user control over their data)
- Security (follow the best practices of protecting user data and using platform-specific features)
During the past few years, I’ve seen a growing demand from app developers for learning how to build end-to-end encryption into their apps.
Companies do not want to access their users’ data on the backend, so they prefer to implement application-side encryption before transferring the data to the server. Large enterprises build cryptographically driven transparency to prove to users that their data is used correctly.
Luckily, modern encryption libraries have all of the required building blocks and are easy to use — try Apple’s own CryptoKit for apps in the Apple ecosystem, or Themis for multi-platform apps.
App review guidelines
Apple’s app review guidelines were updated again too. These two points have been attracting many people’s attention: account deletion and social network revocation.
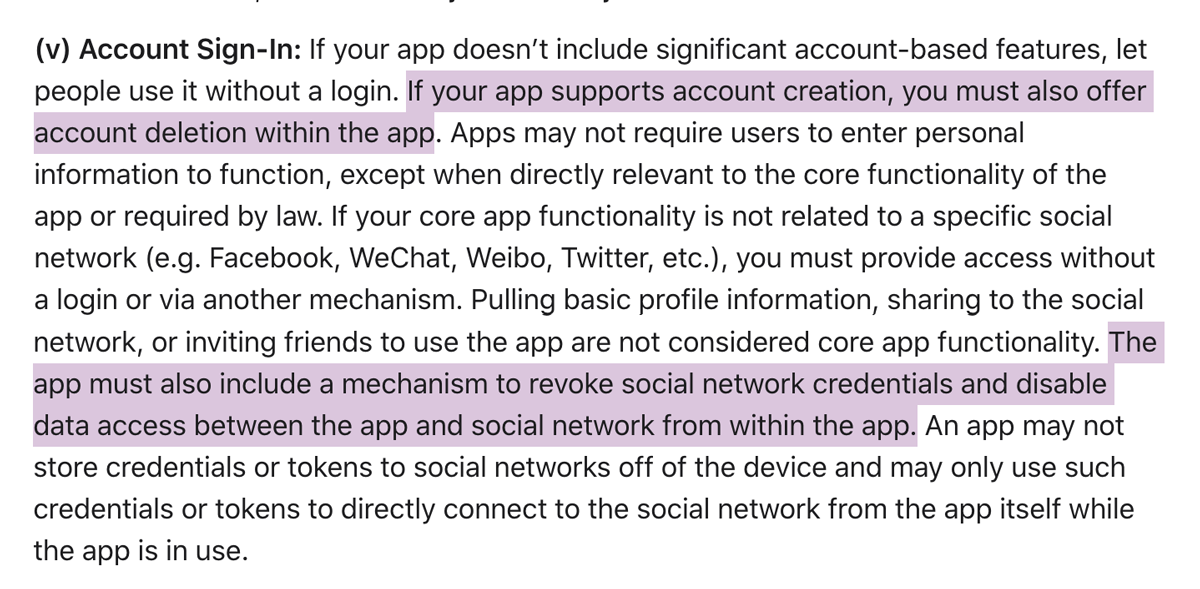
Pay attention to the “within the app” phrase. It means that the common workaround of ”please send us an email if you'd like to delete your account”, won’t be an option anymore. These changes will become required starting in September 2021.
API changes
Want to find out which APIs that were changed? Apple’s documentation portal has a mode to show all changes.
If you use CloudKit within your apps, then take a look at this new API for encrypting any data types that are stored in iCloud. Strings, numbers, dates, CLLocation values and arrays are supported:
// Device 1: Encrypt the data before calling CKModifyRecordsOperation
myRecord.encryptedValues["encryptedStringField"] = "Sensitive value"
// Device 2: Decrypt the data after calling CKFetchRecordsOperation
let decryptedString = myRecord.encryptedValues["encryptedStringField"] as? String
The above sample code is from Apple’s “Privacy pillars in focus” session.
The above API implements a “client-side encryption” pattern, enabling you to encrypt your app’s data before transmitting it over the network, using encryption keys bound to a device.
Videos
Oh, developers. WWDC is a time to watch! I enjoy the new shorter video format (15-30 min), it makes it easier for me to watch a few videos in a row.
Here are links to the privacy and security-related videos that I either have watched or am planning to watch.
Privacy
- Apple’s privacy pillars in focus
- Meet privacy-preserving ad attribution
- Get ready for iCloud Private Relay
Security
- Mitigate fraud with App Attest and DeviceCheck.
- Move beyond passwords
- Use Accelerate to improve performance and incorporate encrypted archives
- Safeguard your accounts, promotions, and content
- Secure login with iCloud Keychain verification codes
Misc
Summary
Apple continues to push security and privacy-related topics, giving developers more tools and better APIs. Now it’s our time to shine ☀️
Let me know what your favorite security or privacy-related features are, what you think about new APIs, or just say hello on Twitter.
Also, don’t forget to follow these engineers that are into security: @julepka, @florentmorin, @patrickwardle, @FredericJacobs, @ivRodriguezCA, @j08ny, @devstefops, @clevybencheton, and @Jaymzu.
Thank you, stay secure, use encryption! 🧡
 Bitrise
BitriseAutomatically build, test and distribute your app on every Pull Request, and use a powerful new suite of add-ons to visualize your test results, to ship your app with ease, and to add crash and performance monitoring to your project. Get started for free.

